Introduction
Technology is evolving so fast that smartphones were once ponderous devices; now they are massive parts of our daily lives. We depend on them, as they have become ubiquitous in our business and social lives. Every new technology raises security risks, and keeping up with such changes is the security industry’s critical problem. Our industry has gained a deeper understanding of the mobile threat landscape over time.
Mobile security, it turns out, is all about data protection. When you compromise someone’s smartphone, you gain unfiltered access to their life. Therefore, a mobile app security standard must focus on how these applications manage, store, and protect sensitive data.
iOS and Android offer mature APIs for secure data storage and communication, but they must be implemented and used correctly to be effective. What matters is how far one should go to ensure data confidentiality and integrity. The MASVS is a venture by OWASP to standardize these requirements to fit different security scenarios.
What is MASVS – The Mobile Application Security Verification Standard?
The OWASP Mobile Application Security Verification Standard (MASVS) is a security industry standard for mobile applications developed by the Open Worldwide Application Security Project (OWASP). It means addressing the most common mobile application security threats by providing a complete set of security criteria.
The MASVS standard covers the essentials of the mobile app attack surface against reverse engineering and tampering. The MASVS is useful in piloting the mobile app development process though it’s not 100% industry consensus.
The MASVS is an invaluable tool designed to be used as a metric, guidance, or during procurement for mobile app security verification, serving as a valuable resource for software and security professionals. The objective of MASVS is to enhance the security of mobile applications while also providing defence-in-depth against client-side issues.
Check out the official document by OWASP to read more about the assumptions, secure app Ecosystem, applicability, and role of automated security testing tools.
Mobile Application Security Model
The standard divides into different groups and defines the most crucial areas of the mobile attack surface. Several MASVS-XXXXX labelled control groups provide guidance and standards in the following areas:
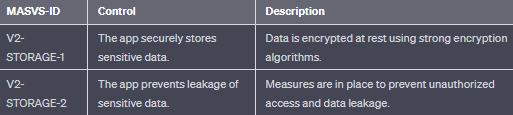
- MASVS-STORAGE: Secure storage of sensitive data on a device (data-at-rest).
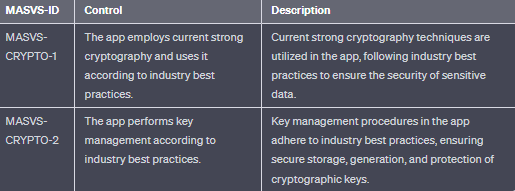
- MASVS-CRYPTO: Cryptographic functionality used to protect sensitive data.
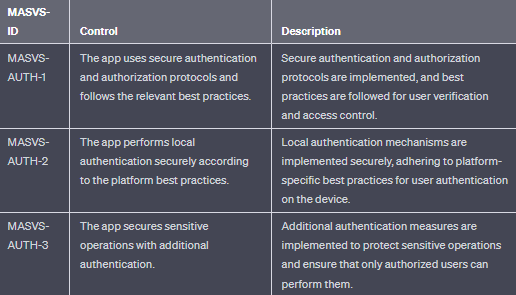
- MASVS-AUTH: Authentication and authorization mechanisms used by the mobile app.
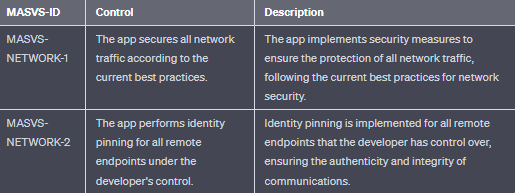
- MASVS-NETWORK: Secure network communication between the mobile app and remote endpoints (data-in-transit).
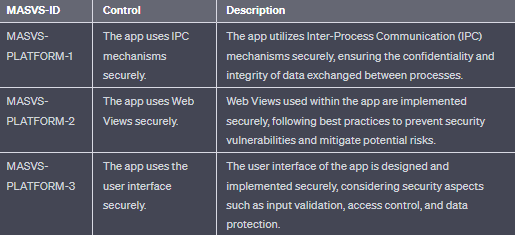
- MASVS-PLATFORM: Secure interaction with the underlying mobile platform and other installed apps.
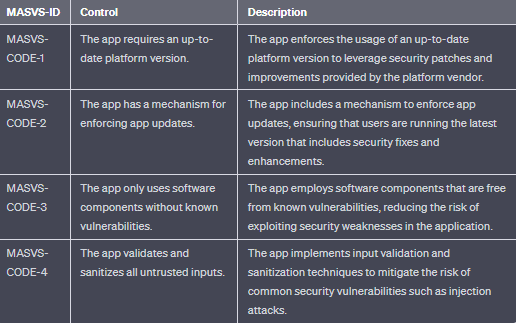
- MASVS-CODE: Security best practices for data processing and keeping the app up to date.
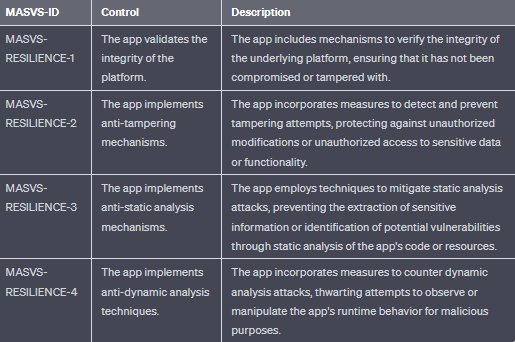
- MASVS-RESILIENCE: Resilience to reverse engineering and tampering attempts.
Each control group has its controls labelled MASVS-XXXXX-Y that assist in implementing the specific security measures needed to achieve compliance. There are links to the MASTG test cases for each MASVS control in the OWASP Mobile Application Security Checklist.
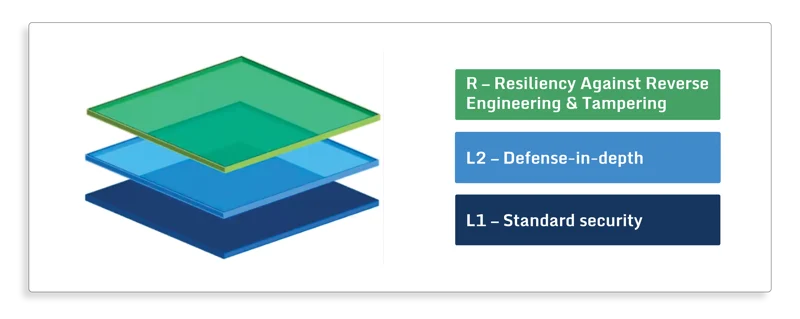
OWASP Security Levels
L1, L2, and Resilience are the three levels of compliance defined by MASVS.
OWASP MASVS Categories
The MASVS security requirements are grouped into eight categories, from V1 to V8.
- V1: Architecture, Design and Threat Modeling Requirements
- V2: Data Storage and Privacy Requirements
- V3: Cryptography Verification Requirement
- V4: Authentication and Session Management Requirements
- V5: Network Communication Requirements
- V6: Environmental Interaction Requirements
- V7: Code Quality and Build Setting Requirements
- V8: Resiliency against Reverse Engineering Requirements
Closing Thoughts
The OWASP MASVS standard provides guidance on security levels for different threat scenarios. Furthermore, MASVS can automate unit and integration tests and replace off-the-peg secure coding lists.
Codersperhour prioritizes security throughout all stages of mobile app development, from the initial planning and design phase to deployment and ongoing maintenance. Our mobile development team adheres to secure development best practices, prioritizing sensitive data protection and addressing security vulnerabilities that could be a target. Contact us today to develop your startup, enterprise, gaming, or social media networking apps. We guarantee robust, scalable protection for apps without compromising app performance.


